Untangle + APC
Untangle® and APC™ have partnered to offer comprehensive network protection at the edge. Together we provide
enterprise level protection from some of the leading causes of network downtime. Powerful product yet simple
enough that it is ideal for organizations with limited IT resources.
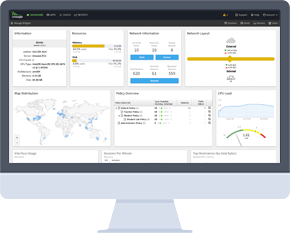
Simple Yet Powerful Unified Threat Management
Untangle’s NG Firewall is a unified threat management solution that takes the complexity out of network security–saving you time, money and frustration. Get everything you need in a single, modular platform that fits the evolving needs of your organization without the headaches of multiple point solutions.
Comprehensive security at the gateway
Antivirus, IPS/IDS, web filtering, application control, bandwidth shaping, captive portal, multiple VPN options and more on a single appliance.
Data-base driven reporting for deep analysis and insights
Included on the appliance, no flat log files. Drill down into any level of detail about users, groups, devices, hosts, and sessions. Create widgets and pin to the dashboard for easy visibility.
Easy to use with configuration from a single screen
Setup <10 minutes with configuration wizards and intelligent default settings. Policy management is easy with top-down approach and inheritance.
Secure, flexible deployment options
Turnkey appliances, 3rd party hardware, virtualized environments or AWS Software is open source under GPL2, so auditable and secure with no backdoors.

Integrated Cloud Services
Untangle delivers a growing range of services that amplify the power of your NG Firewall deployments. These cloud-based products are seamlessly integrated with NG Firewall requiring no additional hardware on premise.
Manage multiple locations remotely with Command Center
Push policies, audit logins, set up alerts, see threat notifications from multiple firewalls on a single pane of glass. No server required.
Integrated cloud scan threat intelligence with ScoutIQ™
Provides an extra layer of security based on threats seen in the wild from real-world deployments and data feeds.